MDE is unique among threat protection products for Windows in that it uses the sensors built into Windows 10 and Windows 11 to communicate with the Defender cloud analytics services. The MDE agent is available as a standalone application for Android, Linux, macOS, and iOS devices.
The following table lists the supported versions of various platforms (though not all features or capabilities are available across all platforms):
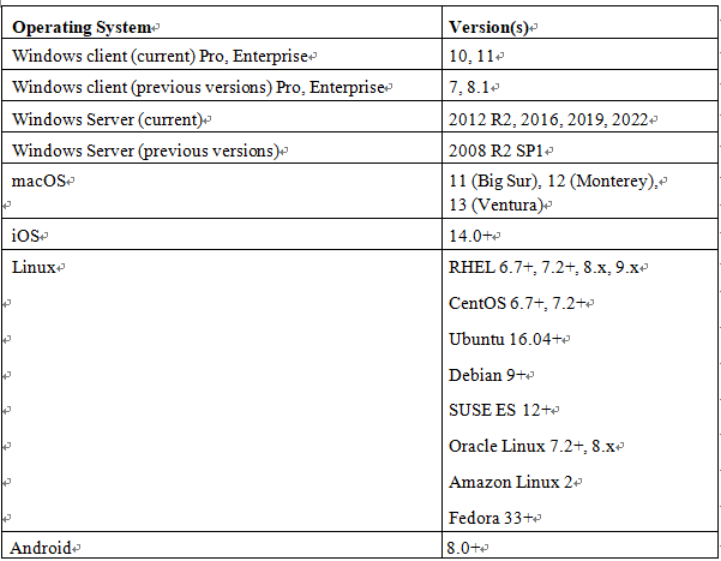
Table 9.1 – MDE-supported platforms
Deployment of MDE on platforms besides Windows 10 or Windows 11 will require additional software, such as the MDE client for iOS or Android, Microsoft Monitoring Agent(MMA) for down-level Windows devices, or the Defender for Endpoint deployment packages for macOS or Linux.
Further Reading
There are many features available as part of EDR or AIR that may not be available on all platforms. Also, there may be differences in feature performance or capability based on whether MDE P1 or P2 is used. To review the differences, see the following resources:
- Defender for Endpoint-supported capabilities by platform: https://learn.microsoft. com/en-us/microsoft-365/security/defender-endpoint/supported-capabilities-by-platform.
- Vulnerability management plans and capabilities: https://learn.microsoft.com/ en-us/microsoft-365/security/defender-vulnerability-management/ defender-vulnerability-management-capabilities.
Next, you’ll briefly look at the deployment architectures.
Deployment Architectures
MDE can be deployed in a variety of ways, depending on how your organization is currently configured, what type of infrastructure is in use, and what management tools are available.
For example, your infrastructure architecture may fall into one of the following categories:
- Cloud-first or cloud-native
- Co-management or hybrid
- On-premises
From a management perspective, you may be able to deploy using one or more of the following methods:
- Local scripting (recommended for up to 10 devices)
- Group policy
- Microsoft Intune or anothermobile device management (MDM) platform
- Microsoft Configuration Manager or a third-party software deployment platform
- Virtual desktop infrastructure (VDI) platform servicing
Before you begin planning deployment and onboarding activities, you will need to understand how your environment is currently designed and what your strategy for management is going to be, as well as what licensing subscription level you will use. Once you have identified those requirements and components, it’s time to start planning a deployment and what Defender for Endpoint settings will be configured.
Configuring Defender for Endpoint Settings
MDE has a myriad of settings that allow you to manage features across multiple platforms and software features.


Leave a Reply